In the realm of cybersecurity, few threats are as stealthy and insidious as rootkits. These clandestine software packages are designed to conceal malicious activity and provide unauthorized access to a compromised system or network. In this article, we delve into the shadowy world of rootkits, uncovering their clandestine operations, detecting their presence, and fortifying network defenses against their infiltration.
What is a Rootkit?
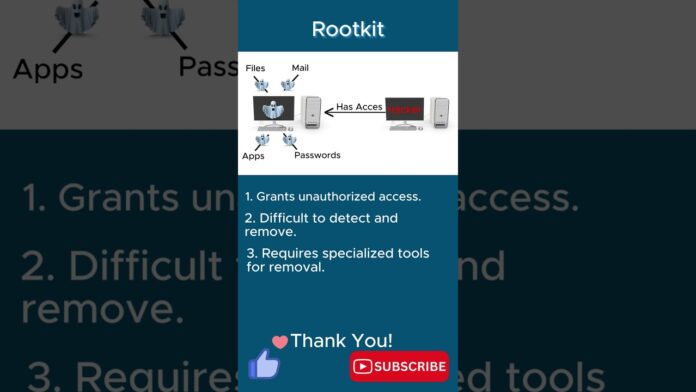
A rootkit is a collection of software tools and techniques used by attackers to gain privileged access to a computer system or network while concealing their presence from users and security mechanisms. Rootkits operate at the deepest levels of the operating system, known as the kernel, enabling attackers to manipulate system functions, evade detection, and maintain persistent control over compromised systems.
How Do Rootkits Work?
Rootkits employ various methods to infiltrate and subvert system security, including:
- Kernel-Level Exploitation: Rootkits exploit vulnerabilities in operating system kernels to gain privileged access and execute malicious code without detection.
- Stealth Techniques: Rootkits employ stealthy tactics to evade detection by antivirus software and intrusion detection systems (IDS), including hiding processes, files, registry keys, and network connections.
- Backdoor Installation: Rootkits often include backdoor functionality, enabling attackers to remotely access and control compromised systems for nefarious purposes, such as data theft, espionage, or launching further attacks.
Types of Rootkits:
- User Mode Rootkits: These rootkits operate at the user level, modifying system libraries, binaries, or configuration files to hijack system functions and conceal malicious activity.
- Kernel Mode Rootkits: Kernel mode rootkits operate at the operating system’s kernel level, directly manipulating system memory structures, drivers, or system calls to gain deep-rooted access and control over the system.
- Bootloader Rootkits: Bootloader rootkits infect the system’s bootloader or firmware, enabling attackers to subvert the boot process and load malicious code before the operating system initializes, evading detection and control.
Detecting and Mitigating Rootkits:
Detecting and mitigating rootkits requires a multi-layered approach to network security, including:
- Endpoint Protection: Deploy robust antivirus, antimalware, and endpoint detection and response (EDR) solutions to detect and block rootkit threats at the endpoint.
- Behavioral Analysis: Implement behavioral analysis techniques to monitor system behavior and identify anomalous activities indicative of rootkit infection, such as unauthorized process execution or system file modifications.
- Rootkit Scanners: Utilize specialized rootkit scanning tools to perform deep scans of system memory, files, and registry entries to detect and remove rootkit components from compromised systems.
- Secure Boot and Firmware Protection: Enable secure boot mechanisms and firmware integrity checks to prevent bootloader rootkits from infecting system firmware and subverting the boot process.
Rootkits represent a significant and persistent threat to network security, leveraging stealthy techniques to evade detection and maintain persistent access to compromised systems. By understanding the tactics and behaviors of rootkits, implementing proactive security measures, and leveraging advanced detection and mitigation techniques, organizations can fortify their defenses against these covert adversaries and safeguard their networks from the pernicious effects of rootkit infections. In the ever-evolving landscape of cybersecurity, vigilance, resilience, and collaboration are essential in the ongoing battle against rootkit threats, ensuring the integrity, confidentiality, and availability of network resources and data.